In this part I'll tell you about the development approach we chose.
To avoid the situation when a framework is being built according to some pure theoretical ideas and as a result it is hard to use it in real world scenarios we had decided to start from the other side: try implementing an application that seems to be more or less real, put into practice our security concepts and thus develop the security system.
We chose Northwind database model as a playground and slightly modified it to add some complexity in company staff relationships.
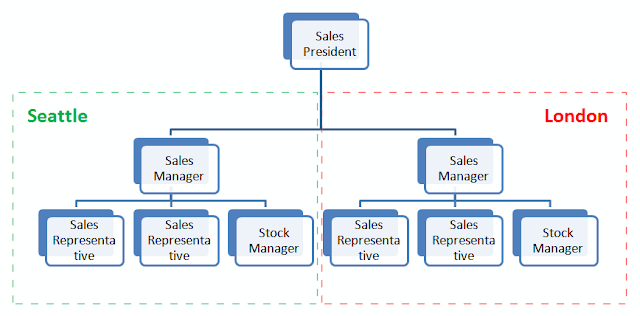
Here is the updated organization chart for our Northwind company.
There are 2 sales departments: first is located in Seattle and second is in London. Both of them are managed by a sales manager, each of them has 2 sales representatives and 1 stock manager. Sales representatives report to sales manager, both sales managers report to sales president.
In this application model we defined the following main types of entities to secure:
- Customer
- Order
- Product
- Employee
Next we have to define which company staff will have access to these secured entities, and which won't. Moreover, there might be several levels of access, for example, read, write and any other more specific ones.
According to the organization chart, we define 4 main roles:
- Stock manager
- Sales representative
- Sales manager
- Sales president
- All staff has read-only access to employees data.
- Stock managers manage products. They doesn't have access to customers and orders.
- Sales representatives have read-only access to products, have full access to customers of their sales department and their own orders. They don't have access to order approval.
- Sales managers also have full access to customers of the sales department, to their own orders and well as to orders of sales representatives in their sales department. Moreover, sales managers have access to the order approval operation.
- Sales president has access to all kind of information without limitation, but in read-only mode. In addition, he can manage employees (hire, dismiss, so he also has write access).
This matrix that demonstrates the additional limitations that must be met as well.
So, here is the deal: we need to provide a flexible and efficient security framework that can be used in domain models like this one with all above-mentioned permissions and limitations. In the next post I'll show you whether we managed to achieve the goal and how we did it.






Cant wait for another post, when will you post it?
ReplyDeletePatience, Peter. Will post the next one this week, I hope.
ReplyDeleteBeautiful! Can't wait too. This will be useful.
ReplyDeleteThis comment has been removed by the author.
ReplyDeletehmm, part3 where are you?
ReplyDeleteThanks for your interest, guys. It is coming soon.
ReplyDeleteNot sure it will be published today, more likely the beginning of the next week.
Your article has proven useful to me. It’s very informative and you are obviously very knowledgeable in this area. You have opened my eyes to varying views on this topic with interesting and solid content. identity access management products
ReplyDeleteThe security administrations utilize the most recent innovation and very gifted staff and security experts who can be trusted for great administrations.Best Security Place reviews
ReplyDeletesdasd
ReplyDeleteThey provide high quality, revolutionary as well as sophisticated safety as well as existence security devices such as fireplace as well as smoke cigarettes devices, movie monitoring, motion sensors, glass-break sensors and residential automation technologies like electronic door hair. You can also take advantage of professional guidance in choosing the very best solution for your house by talking to the actual company’s safety specialists http://www.best-5-home-security-companies.com/protect-america.
ReplyDeleteThis article will discuss through an introduction of security development, how we can feel a little safer about the security we implement in our systems 먹튀검증
ReplyDeleteThanks for sharing this post. Kanhasoft is top notch software company offering offshore .net development services in India. We are expert in creating robust and reliable Dot net web application at affordable price. Visit our site to know more about us.
ReplyDeleteNetwork Security is the next wave which is bound to sweep the software market. Securing the network is an art by itself www.findmeasecuritycompanyin.com
ReplyDeleteIn that circumstance, the team-building model can be coordinated at setting up generally speaking work assemble objectives, which influence both individual and collective endeavor and conduct, and, at last, the execution results at both the person, and additionally the gathering level. team building
ReplyDeleteA portable fish finder is a good choice if you don't fish from the same ship all the time. https://internetprivatsphare.ch
ReplyDeleteAppreciating the persistence you put into your blog and detailed information you provide. I’ve bookmarked your site and I’m adding your RSS feeds to my Google account. les meilleurs vpn
ReplyDeleteI have used a lot of juicers in the past and I created this blog to help juice lovers make the right decision in choosing the type of juicer that best fit their needs. There are several good masticating juicers to choose from. vpn reviews
ReplyDeleteI am glad to locate your recognized method for composing the post. Presently you make it simple for me to comprehend and actualize the idea. Much obliged to you for the post. https://privacyonline.fi
ReplyDeleteI was taking a gander at some of your posts on this site and I consider this site is truly informative! Keep setting up..
ReplyDeletealarms Dublin
Incredible articles and awesome design. Your blog entry merits the greater part of the positive input it"s been getting. thebestvpn
ReplyDeleteI have read your blog it is very helpful for me. I want to say thanks to you. I have bookmark your site for future updates. https://internetprivatsphare.at
ReplyDeleteCriminals are getting more and more creative and ingenious with their modus operandi and becoming much more proficient in disabling security features. Locksmith
ReplyDeleteA fascinating dialog is value remark. I feel that it is best to compose more on this matter, it may not be an unthinkable theme however generally people are insufficient to chat on such subjects. To the following. Salud. vpnveteran.com
ReplyDeleteHave you thought about how people get rich? NOT? And you go to BGAOC and try to win and not be defeated. real casino only here The most perfect feeling is to play and get paid for it.
ReplyDeleteSpy cams used to be big, bulky and impractical to use. Nowadays, they are all about compactness and portability - the smaller they are and easier to conceal, the better. Erica
ReplyDeleteNice post! This is a very nice blog that I will definitively come back to more times this year! Thanks for informative post. Finde mehr heraus
ReplyDeleteI really enjoy simply reading all of your weblogs. Simply wanted to inform you that you have people like me who appreciate your work. Definitely a great post. Hats off to you! The information that you have provided is very helpful. internet privatsphare
ReplyDeleteA good blog always comes-up with new and exciting information and while reading I have feel that this blog is really have all those quality that qualify a blog to be a one. lemigliorivpn
ReplyDeleteIts an incredible joy perusing your post.Its brimming with data I am searching for and I want to post a remark that "The substance of your post is marvelous" Great work. deze website
ReplyDeleteI am really enjoying reading your well written articles. It looks like you spend a lot of effort and time on your blog. I have bookmarked it and I am looking forward to reading new articles. Keep up the good work. security company leek
ReplyDeleteGreat post, and great website. Thanks for the information! Alarms in Parramatta
ReplyDeleteExcellent blog and I really glad to visit your post. Keep continuing...
ReplyDeleteEmbedded System Course Chennai
Embedded Systems Course
Unix Training in Chennai
Power BI Training in Chennai
Pega Training in Chennai
Spark Training in Chennai
Linux Training in Chennai
Tableau Training in Chennai
Oracle Training in Chennai
Appium Training in Chennai
Graphic Design Courses in Chennai
Embedded Training in OMR
http://gbasibe.com
ReplyDeletehttp://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
ReplyDeletehttp://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
http://gbasibe.com
Liên hệ Aivivu, đặt vé máy bay tham khảo
ReplyDeleteVe may bay di My
chuyến bay hồi hương từ mỹ về việt nam
chuyến bay thương mại từ canada về việt nam
giá vé máy bay nhật việt vietnam airline
Lịch bay từ Seoul đến Hà Nội
Vé máy bay từ Đài Loan về VN
khách sạn cách ly ở tphcm
Look advanced to far added agreeable from you Thanks for finally writing about 토토커뮤니티
ReplyDeleteIt's always coming. This blog is great 먹튀검증 Your post has really helped me a lot
ReplyDeletesite. Plenty of helpful info here. I’m sending it to several pals ans also sharing in delicious. And certainly, thanks to 토토사이트검증 Thank you guys for sharing
ReplyDeleteWow, superb blog layout! How long have you been blogging for? you make blogging look easy. The overall look of your site is 먹튀검증
ReplyDeleteI was unable to oppose remarking. Totally composed!best interiors
ReplyDeleteMy partner and I stumbled over here coming from a different website and thought I may as well
ReplyDeletecheck things out. I like what I see so now i'm following
you. Look forward to exploring your web page again. 출장안마
Always so interesting to visit your site.What a great info, thank you for sharing. this will help me so much in my learning localizacion satelital
ReplyDeleteThank you for sharing this information. I read your blog and I can't stop my self to read your full blog. Again카지노사이트 Thanks and Best of luck to your next Blog in future.
ReplyDeleteAn outstanding share! I have just forwarded this onto a co-worker who was doing a little homework on this. And he actually bought me dinner simply because I discovered it for him… lol. So let me reword this…. Thanks for the meal!! But yeah 야동 , thanks for spending some time to talk about this topic here on your web site.
ReplyDeleteIts like you read my mind! You appear to know so much about this, like you wrote the book in it or something. I think that you can do with some pics to drive the message home a bit 대딸방, but instead of that, this is magnificent blog. An excellent read. I’ll definitely be back.
ReplyDeleteI am also commenting to make you understand what a notable experience my friend’s child gained studying your webblog. She realized so many things, with the inclusion of what it is like to have a marvelous giving character to make men and women completely fully grasp some tricky subject matter. You undoubtedly surpassed readers’ expected results 마사지블루. Thank you for offering those great, healthy, educational as well as fun thoughts on your topic to Emily.
ReplyDeleteHello There. I found your blog using msn. This is a really well written article. I will be sure to bookmark it and come back to read more of your useful info. Thanks for the post. I’ll definitely return.건마탑
ReplyDeleteThanks for the sensible critique. Me & my neighbor were just preparing to do a little research on this. We got a grab a book from our local library but I think I learned more from this post. I am very glad to see such great info being shared freely out there.
ReplyDelete카지노커뮤니티
>cc
You have terrific composing abilities. I'm so pleased to locate the very same subject I have actually been seeking. Every person is providing me a great deal of praises now. You're outstanding. As an author, you're so awesome since you're such a fantastic author. Why do not you come and also see my article?바카라사이트
ReplyDeleteWhat a post I've https://pbase.com/topics/alskds/taco_cat_goat_cheese_pizza
ReplyDeletebeen looking for! I'm very happy to finally read this post. 안전놀이터 Thank you very much. Can I refer to your post on my website? Your post touched me a lot and helped me a lot. If you have any questions, please visit my site and read what kind of posts I am posting. I am sure it will be interesting.
This is the perfect post.메이저토토사이트 It helped me a lot. If you have time, I hope you come to my site and share your opinions. Have a nice day.
ReplyDeleteThat's a really impressive new idea! 메이저토토사이트추천 It touched me a lot. I would love to hear your opinion on my site. Please come to the site I run once and leave a comment. Thank you.
ReplyDelete
ReplyDeleteThis site seems to inspire me a lot. Thank you so much for organizing and providing this quality information in an easy to understand way. I think that a healthy era of big data can be maintained only when such high-quality information is continuously produced. And I, too, are working hard to organize and provide such high-quality information. It would be nice to come in once and get information.
Also visit my site:토토
I'm so happy to finally find a post with what I want. 메이저토토사이트 You have inspired me a lot. If you are satisfied, please visit my website and leave your feedback.
ReplyDeleteHi there, I simply hopped over in your website by way of StumbleUpon. Now not one thing I’d typically learn, but I favored your emotions none the less. Thank you for making something worth reading. 먹튀검증업체
ReplyDeleteExcellent read, I just passed this onto a friend who was doing a little research on that. And he actually bought me lunch as I found it for him smile Therefore let me rephrase that: Thank you for lunch. 먹튀신고
ReplyDeleteYou made some good points there. I did a Google search about the topic and found most people will believe your blog. 메이저사이트
ReplyDeleteI finally found what I was looking for! I'm so happy. 안전한놀이터 Your article is what I've been looking for for a long time. I'm happy to find you like this. Could you visit my website if you have time? I'm sure you'll find a post of interest that you'll find interesting.
ReplyDeleteI'm impressed, I must say. Actually rarely can i encounter a blog that's both educative and entertaining, and without a doubt, you could have hit the nail about the head. Your idea is outstanding; the thing is something that too few individuals are speaking intelligently about. We are delighted that we came across this around my try to find some thing with this.메이저사이트
ReplyDeleteThanks for an interesting blog. What else may I get that sort of info written in such a perfect approach? I have an undertaking that I am just now operating on, and I have been on the lookout for such info 먹튀검증 It's amazing. I want to learn your writing skills. In fact, I also have a website. If you are okay, please visit once and leave your opinion. Thank you.
ReplyDeleteI figure this article can be enhanced a tad. There are a couple of things that are dangerous here, and if you somehow managed to change these things, this article could wind up a standout amongst your best ones. I have a few thoughts with respect to how you can change these things. 메이저놀이터
ReplyDeleteYou make so many great points here that I read your article a couple of times. Your views are in accordance with my own for the most part. This is great content for your readers. 안전놀이터
ReplyDeleteAmazing article..!! Thank you so much for this informative post. I found some interesting points and lots of information from your blog. Thanks 메이저놀이터
ReplyDeleteThank you a bunch for sharing this with all of us you actually realize what you are talking about! Bookmarked. Please also seek advice from my site =). We could have a hyperlink change contract between us 안전놀이터
ReplyDelete토토 I recently found many useful information in your website especially this blog page. Among the lots of comments on your articles. Thanks for sharing
ReplyDelete바카라사이트 Hurrah! Finally I got a webpage from where I know how to genuinely take valuable facts concerning my study and knowledge.
ReplyDelete온라인카지노
ReplyDeleteThank you for your post, I look for such article along time, today i find it finally. this post give me lots of advise it is very useful for me. nice i like it.
Howdy! Someone in my Myspace group shared this website with us so
ReplyDeleteI came to give it a look. I'm definitely loving the information. I'm bookmarking and will be tweeting this to my followers!
Superb blog and superb design and style.
Feel free to surf to my blog - 경마사이트
Your ideas inspired me very much. roulette It's amazing. I want to learn your writing skills. In fact, I also have a website. If you are okay, please visit once and leave your opinion. Thank you.
ReplyDeleteI saw your article well. You seem to enjoy 카지노사이트 for some reason. We can help you enjoy more fun. Welcome anytime :-)
ReplyDeleteNice to meet you. Your website is full of really interesting topics. It helps me a lot. I have a similar site. We would appreciate it if you visit once and leave your opinion. 카지노게임
ReplyDeleteI've been looking for photos and articles on this topic over the past few days due to a school assignment, 우리카지노 and I'm really happy to find a post with the material I was looking for! I bookmark and will come often! Thanks :D
ReplyDeleteThere are various writings here and there are many articles that can be developed. I m going to press recommendations. 안전토토
ReplyDeleteWhy is there so much good information? l keep that in mind. 토토사이트
ReplyDeleteExtremely overall quite fascinating post. I was searching for this sort of data and delighted in perusing this one.스포츠토토
ReplyDeleteNice information, valuable and excellent design, as share good stuff with good ideas and concept토토사이트
ReplyDeleteWhile looking for articles on these topics, I came across this article on the site here. As I read your article, I felt like an expert in this field. I have several articles on these topics posted on my site. Could you please visit my homepage? Nhà cái lừa đảo
ReplyDeleteI merely stumbled upon your internet site and wanted to say that I’ve very favored learning your weblog posts.
ReplyDelete룰렛사이트탑
I find the development approach good on this one. But I would like to study it a lot further. Greetings from Roofers Kamloops
ReplyDeleteExcellent write-up. I absolutely appreciate this website. 토토
ReplyDeleteI find this article really helpful. It seems to be of better quality than the articles on other websites. It seems that the author knows how much effort went into writing this article.먹튀없는 토토사이트
ReplyDeletei found for that excuse many tempting stuff in your blog particularly its ventilation. Malwarebytes Premium Key is a best Anti-malware software.This software provides businesses with full attack chain protection against.... Malwarebytes Anti Malware Premium Keys
ReplyDeleteWhat a fantabulous observe this has been. in no way seen this understandable of beneficial claim. i'm grateful to you and assume more quantity of posts at the side of those. thank you intensely a lot. Brothers Day Quotes
ReplyDeleteoncasino
ReplyDeleteThis comment has been removed by the author.
Deleteสล็อตมือใหม่ ไม่ควรพลาด เพียงทำการเล่นเกมผ่านเว็บไซต์ PGSLOT เล่นได้มาก ไม่ว่าจะเป็นสล็อตออนไลน์ คาสิโนออนไลน์ อาเขต และยิงปลา เล่นได้ตลอด 24 ชั่วโมง เพื่อทดลองเกมใหม่ๆ PG เครดิตฟรี ให้คุณได้ทำการเล่นตลอดทั้งวันๆ ทดลองเล่นก่อนใคร
ReplyDeleteสนุกไม่มีเบื่อ พร้อมรับแจ็คพ็อตก่อนใคร สนุกได้ผ่านเว็บไซต์ PGSLOTออกรางวัลให้ได้เล่นก่อนใคร รับเครดิตฟรี เล่นได้มากกว่า 300 เกม เว็บตรงเล่นได้ไม่ผ่านเอเย่นต์ PG ฟรีเครดิต ทำกำไรได้ตั้งแต่หลักพัน ไปถึงหลักล้าน ฝากถอนสะดวกภายในไม่กี่นาที
ReplyDeleteThis is superb site article its content wa very nice.
ReplyDeleteIdm Crack
ReplyDeleteThanks for sharing with us this important Content.
슬롯사이트
found exactly what I used to be having a look for.
슬롯사이트
ReplyDeleteThis website's content is more useful. And thanks for sharing.
BlueStacks
Your information was very useful to me. Instruction is absolutely a sticky topicI.ou will find a lot of approaches after visiting your post.Will certainly stored and reevaluate your Website. Very interesting to read this article.I would like to thank you for the efforts you had made for writing this awesome article.Great work.
ReplyDeleteelectric masturbator cup
ReplyDeletewill be praised anywhere. I am a columnist This post is really the best on this valuable topic<검증카지노
สูตรบาคาร่า เว็บไซต์คาสิโนออนไลน์ครบวงจร มั่นคงปลอดภัย 100 % เล่นง่าย pg slot ได้เงินไว มีบริการฝากถอนเงินแบบออโต้ เป็นเยี่ยมในผู้ให้ บริการพนันออนไลน์ ซึ่งเป็นบริษัทที่ประดิษฐ์ผลงานเกมส์
ReplyDeleteThanks for sharing such an interesting and useful post.
ReplyDeleteCCNA classes in Pune
Great insights on security systems in this second part! I appreciate the detailed analysis of modern security measures and the emphasis on proactive protection. The discussion on emerging threats and countermeasures is particularly valuable. Looking forward to the next installment—keep up the great work! gamca medical
ReplyDeleteGreat post! Class 8 is such an important year for building strong basics. I’ve noticed students do much better when they get support similar to 8th grade home tutors, especially through a reliable online tuition centre for class 8 where learning is more focused.
ReplyDelete